DNS Management
Border0 provides full DNS management for VPN clients, allowing you to control where DNS queries are resolved, define split DNS rules, and route traffic based on domain names. This gives you fine-grained control over internal and external name resolution while maintaining predictable egress and security visibility.
Overview
When DNS Management is enabled, Border0 takes over DNS configuration for connected VPN clients.
Instead of using the device’s default DNS resolver, Border0 configures a local stub resolver (100.124.100.100) on the client.
That stub resolver forwards DNS queries to the upstream DNS servers defined in your organization settings.
This enables:
- Centralized control over client DNS behavior
- Split DNS resolution for private/internal domains
- Domain-based (DNS) routing through specific connectors
- Predictable egress IPs for selected domains
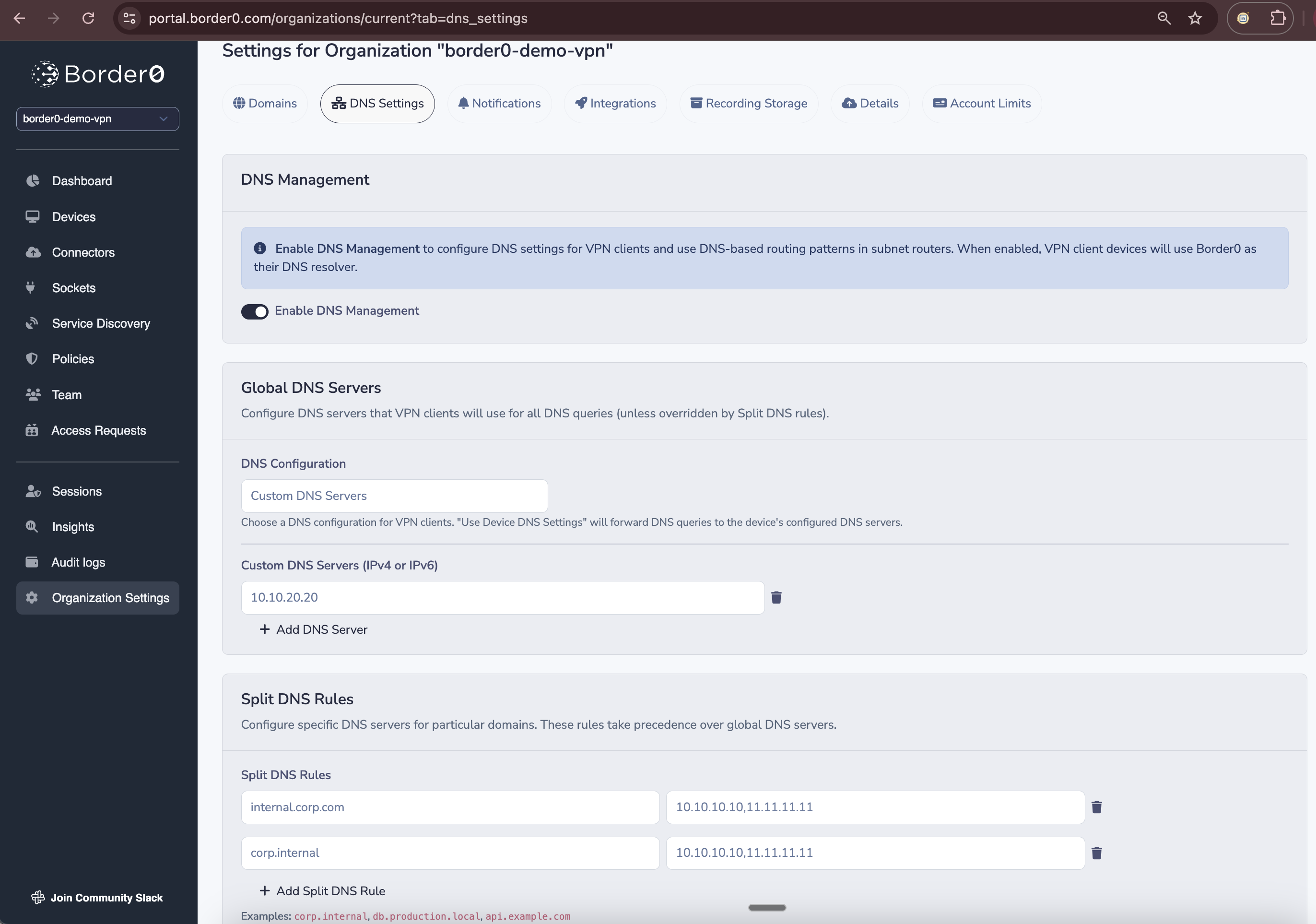
Enabling DNS Management
To enable DNS management:
- In the Border0 Admin Portal, go to
Organization Settings → DNS Settings. - Toggle Enable DNS Management.
- Configure your preferred DNS settings as described below.
Note:
When disabled, clients use their system DNS settings (the OS or network default).
Enabling this feature allows Border0 to manage and override those values when the VPN is active.
Enable DNS management
Global DNS Servers
Global DNS servers define where all DNS queries will be sent, unless a Split DNS Rule applies.
You can choose from:
| Option | Description |
|---|---|
| Cloudflare (1.1.1.1) | Uses Cloudflare’s public resolvers |
| Google (8.8.8.8) | Uses Google’s public resolvers |
| Quad9 (9.9.9.9) | Uses Quad9’s secure resolvers |
| OpenDNS (208.67.222.222) | Uses Cisco OpenDNS resolvers |
| Custom | Specify your own internal or private DNS servers (IPv4/IPv6 supported) |
| Use Device DNS Settings | Leaves DNS resolution to each device’s configured resolver |
Use Custom DNS servers to enable resolving internal domains via your internal DNS servers.
Example Configuration
When DNS management is enabled, VPN clients will send all DNS queries to the Border0 stub resolver at 100.124.100.100. This resolver runs in the local VPN client and forwards them to the upstream DNS servers you selected.
You can verify the configured upstream DNS servers by querying the local stub resolver:
$ dig +short -t txt debug.border0.com @100.124.100.100
"border0: version: v1.1-1849-g5e7d886d date: 20251106"
"upstream: 8.8.8.8:53"
"upstream: 8.8.4.4:53"
"upstream: [2001:4860:4860::8888]:53"
"upstream: [2001:4860:4860::8844]:53"Or use the following debug command:
$ border0 node debug dns
+----------------------+--------------------------------------------+
| SETTING | VALUE |
+----------------------+--------------------------------------------+
| Configured Resolvers | upstream: 8.8.8.8:53 |
| | upstream: 8.8.4.4:53 |
| | upstream: [2001:4860:4860::8888]:53 |
| | upstream: [2001:4860:4860::8844]:53 |
| | upstream: corp.internal=10.10.10.10:53 |
| | upstream: corp.internal=11.11.11.11:53 |
| | upstream: internal.corp.com=10.10.10.10:53 |
| | upstream: internal.corp.com=11.11.11.11:53 |
+----------------------+--------------------------------------------+
| Original DNS Servers | 206.214.246.194:53 |
| | 206.214.246.193:53 |
+----------------------+--------------------------------------------+Split DNS Rules
Split DNS rules let you define specific DNS servers for particular domains.
These rules take precedence over the global DNS configuration.
| Example | Behavior |
|---|---|
internal.corp.com → 10.10.10.10,11.11.11.11 | Queries for *.internal.corp.com will use these DNS servers instead of the global ones |
corp.internal → 10.10.10.10,11.11.11.11 | Same behavior for the corp.internal domain |
Tip:
Use Split DNS for private or internal domains to ensure that internal names resolve only via internal DNS servers, and public names continue using global resolvers.
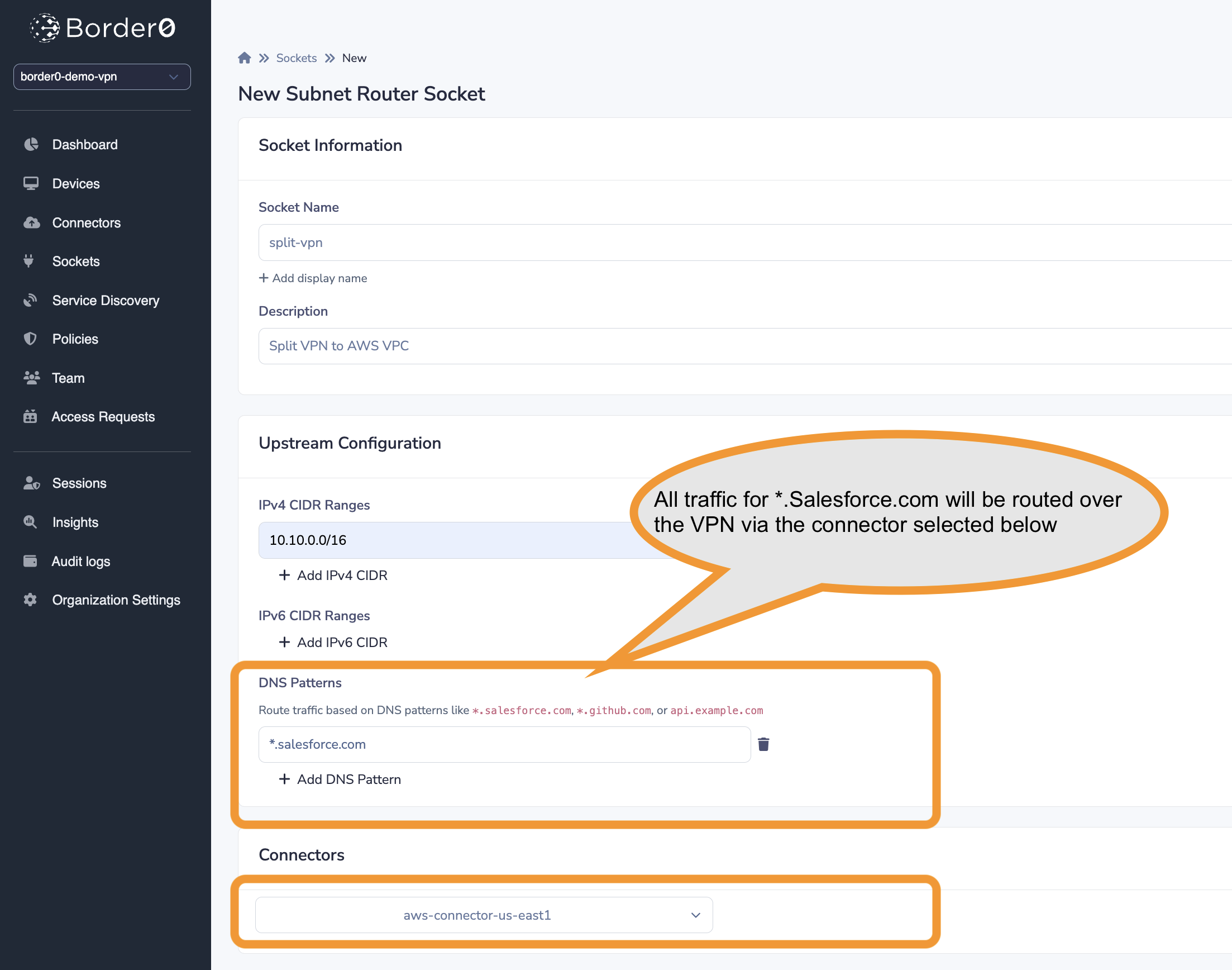
DNS-Based Routing (Domain Patterns)
DNS-based routing allows you to steer traffic based on domain names, not just IP prefixes.
This is useful when you want specific domains (for example SaaS apps such as Salesforce or GitHub) to always route through a designated connector, ensuring consistent egress IP and enforcing access policies. Note that DNS management has to be enabled for this to work.
You can configure DNS-based routing as part of a Subnet Router configuration:
- In the Border0 Admin Portal, go to Sockets → Subnet Router.
- Under Upstream Configuration, you can define both:
- IP Prefixes (for example,
10.11.12.0/24) - DNS Patterns (for example,
*.salesforce.com,*.github.com)
- IP Prefixes (for example,
These domain patterns tell Border0 that any traffic matching those hostnames should be routed through the same connector as the subnet router.
This enables dynamic, name-based routing that automatically adapts as new domains are resolved.
Example
| Pattern | Connector | Purpose |
|---|---|---|
*.salesforce.com | connector-A | Ensure Salesforce traffic exits via a specific egress IP |
*.github.com | connector-B | Make sure GitHub traffic egresses via connector-B |
How it works
When DNS-based routing rules are configured, Border0 handles both DNS resolution and routing updates automatically.
-
Client-side resolution:
The VPN client sends its DNS query to the local Border0 stub resolver (100.124.100.100). -
Forwarding to connector:
The stub resolver recognizes that the domain matches a configured DNS pattern and forwards the query to the associated connector. -
Connector resolution and route setup:
The connector resolves the domain using its own DNS configuration.
Once the domain’s IP addresses are known, the connector automatically updates its local routing configuration to accept and forward traffic from the client to those resolved IPs. -
Client route insertion:
The resolved IPs are returned to the client along with the DNS response.
The client automatically inserts temporary routes for those IPs so that any traffic to the resolved domain is sent through the correct connector. -
Route cleanup:
When those routes are no longer used or the session ends, Border0 automatically removes this dynamic configuration from both the client and the connector.
This automatic process means you don’t need to manage routes manually, Border0 dynamically adds and removes them in real time based on DNS lookups, ensuring traffic for matching domains is always routed correctly.
DNS based routing
How It Works Under the Hood
When DNS Management is enabled:
- Border0 reconfigures the client’s DNS resolver to use
100.124.100.100. - This stub resolver runs locally inside the VPN client.
- It forwards queries to the configured upstream DNS servers (global or split).
- The client OS sees this as its primary nameserver.
Example on macOS
$ scutil --dns
resolver #1
search domain[0] : internal.example.org
nameserver[0] : 100.124.100.100
port : 53
flags : Supplemental, Request A records
reach : 0x00000002 (Reachable)
order : 102600Example Diagnostic Output
$ border0 node debug dns
+----------------------+--------------------------------------------+
| SETTING | VALUE |
+----------------------+--------------------------------------------+
| Configured Resolvers | upstream: 8.8.8.8:53 |
| | upstream: 8.8.4.4:53 |
| | upstream: [2001:4860:4860::8888]:53 |
| | upstream: [2001:4860:4860::8844]:53 |
| | upstream: corp.internal=10.10.10.10:53 |
| | upstream: corp.internal=11.11.11.11:53 |
| | upstream: internal.corp.com=10.10.10.10:53 |
| | upstream: internal.corp.com=11.11.11.11:53 |
+----------------------+--------------------------------------------+
| Original DNS Servers | 206.214.246.194:53 |
| | 206.214.246.193:53 |
+----------------------+--------------------------------------------+
Troubleshooting
Check which DNS server is configured on macOS. When Border0 DNS management is enabled, this should show 100.124.100.100
scutil --dnsFor windows use:
# PowerShell
Get-DnsClientServerAddress
# Or Command Prompt
ipconfig /allVerify stub resolver behavior
dig +short @100.124.100.100 debug.border0.comor, Inspect client DNS configuration
border0 node debug dnsConfirm internal domain resolution
dig internal.corp.com @100.124.100.100Common Issues
Internal domains not resolving → check your Split DNS entries and internal DNS reachability.
Traffic not routing via expected connector → ensure your DNS Patterns match and DNS Management is enabled.
Clients not using stub resolver → confirm that 100.124.100.100 appears as the nameserver on the device.
Updated about 1 month ago
