Managing Credentials and Secrets
Using secret stores to securely store your credentials
When configuring Sockets, sometimes it's needed to configure credentials. These credentials are needed for the connector to, for example authenticate to your upstream database. Credentials are sensitive, so instead of using Border0 to store your upstream credentials, we recommend keeping them local, and use environment variables, your favorite credential managers or secret vaults.
Border0 makes it easy for you to load credentials locally by the connector, so that you can integrate with existing secret managers and don't need to share your credentials with Border0. Instead, the connector can load them dynamically when needed, this way Border0 never sees your credentials.
Supported Secret Sources
The following credentials sources are supported. Note a dynamic credentials always starts with from:
Credential source | credential format | details |
|---|---|---|
Environment variable |
| the environment variable DB_USERNAME will be used as the credential. |
File |
| the string found in the file_/etc/database_username_ will be used as the credential. |
AWS SSM parameter store |
| Here the secret is stored in AWS' SSM parameter store. Using the parameter path /my/path It's important the connector has proper IAM role to read from SSM parameter store |
AWS Secret manager |
| Here the secret is stored in AWS' Secret manager at the secret path /my/path It's important the connector has proper IAM role to read from AWS secret manager. |
Keeper Secrets manager |
| The format is like: The implementation checks both fields and custom_fields to find the matching value. The integration uses the ksm CLI tool, which must be present on the machine and available in PATH. |
Extracting Fields from JSON Secrets with jq_exp
Sometimes secrets are not stored as simple strings, but instead as JSON objects. To support this common pattern, you can use a jq-like expression to extract a specific value from within a JSON structure, regardless of the secret backend.
This is useful when your secret contains multiple fields (like username, password, or nested objects), and you only need one of them.
Syntax
from:<source>:<path>,jq_exp=<expression><source>can be any supported backend, such as aws:secretsmanager, aws:ssm, env, or even file.<path>is the identifier or location of your secret.jq_expis a simple dot-notation expression that extracts a field from the JSON (similar to jq).
Examples
Let’s say your secret looks like this:
{
"username": "apiuser",
"password": "sup3rs3cret!",
"nested": {
"token": "abc123token"
}
}You can reference fields like this:
from:aws:secretsmanager:testsecret,jq_exp=.username
# → apiuser
from:aws:secretsmanager:testsecret,jq_exp=.password
# → sup3rs3cret!
from:aws:secretsmanager:testsecret,jq_exp=.nested.token
# → abc123tokenYou can now selectively extract and apply just the value you need, even from deeply nested secrets.
Tutorial video
Referencing credentials
All fields in the "upstream" configuration settings for a particular socket accept the from: parameter.
Remember, If your secrets starts with from:the Border0 connector will dynamically fetch the secret from the specified source.
Below are some typical examples of where you can use from:to load your credentials locally on the connector in real time.
Socket Type | Field |
|---|---|
SSH - Upstream connection type: standard SSH | SSH Username SSH Password |
Database | Upstream Username Upstream Password Hostname |
AWS credentials | AWS Access Key ID AWS Secret Access Key |
Examples
The screenshot below is an example configuration for a database socket. The credentials the Border0 connector needs to to communicate with the upstream database are dynamically loaded. Specifically the username is loaded from the environment variable RDS_USERNAME while the password is loaded from AWS' SSM parameter store using the path /rdsdata/password
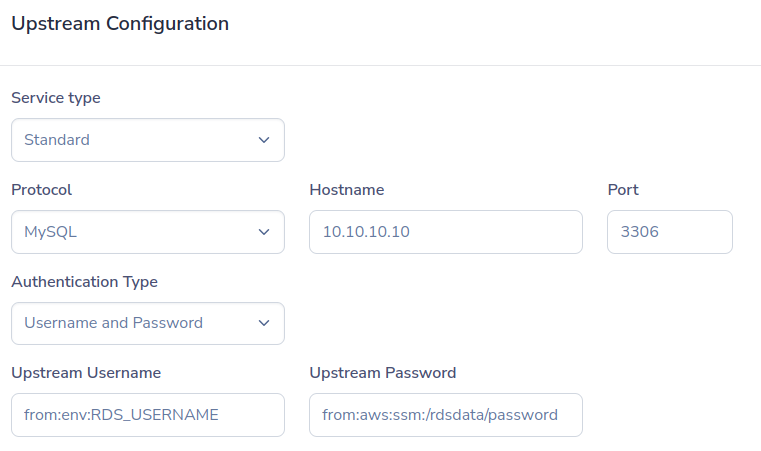
Database credentials loaded from environment variable and AWS SSM parameter store
The Example below shows the upstream configuration for an SSH socket, using username and password authentication as the upstream authentication strategy. Here, instead of statically defining the actual username and password, the connector will load them dynamically. The username will be loaded from the file /etc/ssh_usernameon the connector host. While the password is loaded from AWS' secret manager using the path /staging/sshpassword
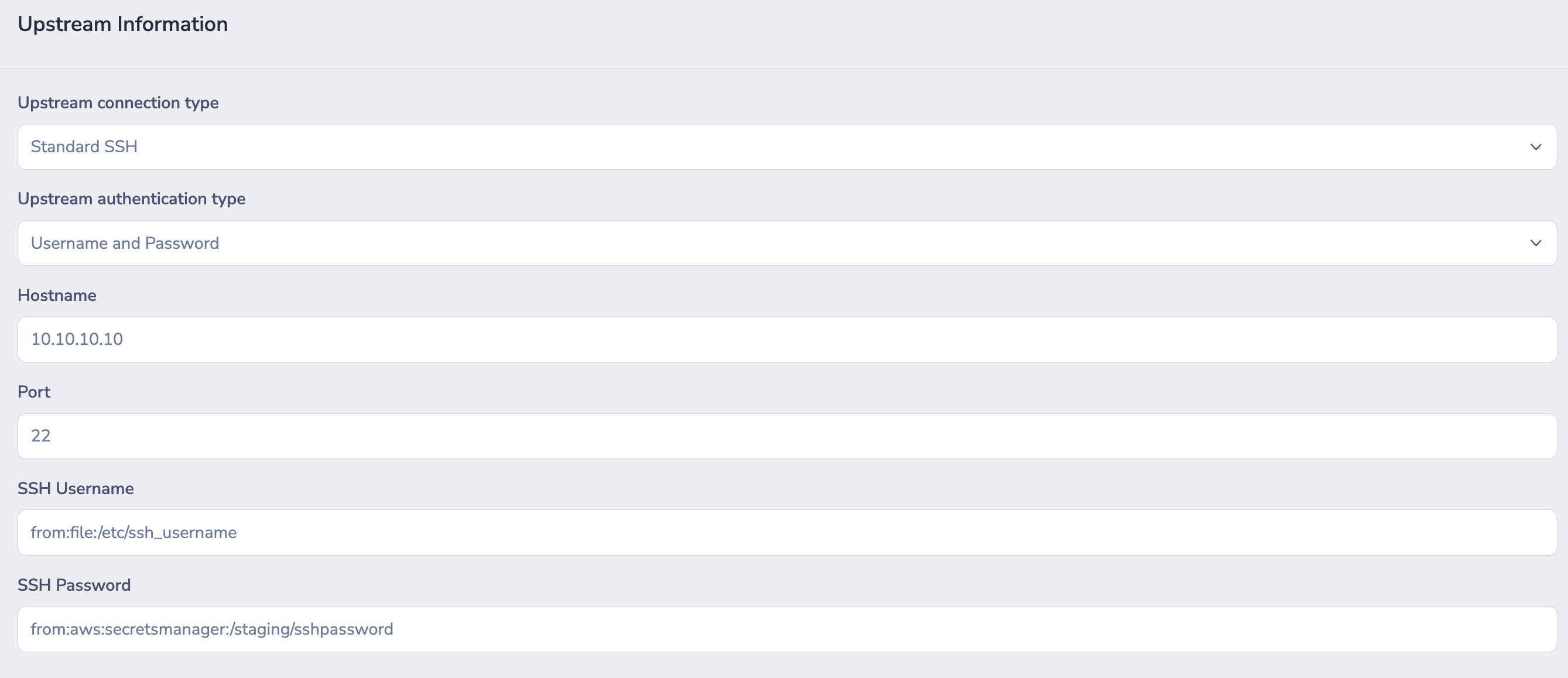
SSH credentials are loaded dynamically by the connector, from the local file system and AWS secret manager.
Extracting secrets from secrets manager:
from:aws:secretsmanager:testsecret,jq_exp=.username --> W$E%^&*V&^EDF
from:aws:secretsmanager:testsecret,jq_exp=.password --> %^&2352626Y)(&^%^
from:aws:secretsmanager:testsecret,jq_exp=.inner_obj.username --> W$E%^&*V&^EDF
from:aws:secretsmanager:testsecret,jq_exp=.inner_obj.password --> %^&2352626Y)(&^%^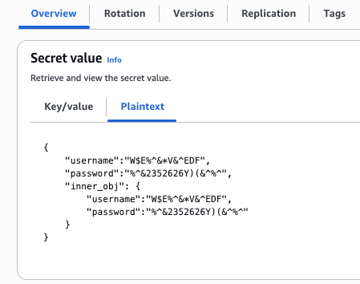
Updated 7 months ago
