Sessions logs
Full Visibility into Your Infrastructure
🔍 Every connection through Border0 is authenticated, and each request is continuously authorized. These connections are what we call sessions and give you full visibility into what’s happening in your environment in real-time.
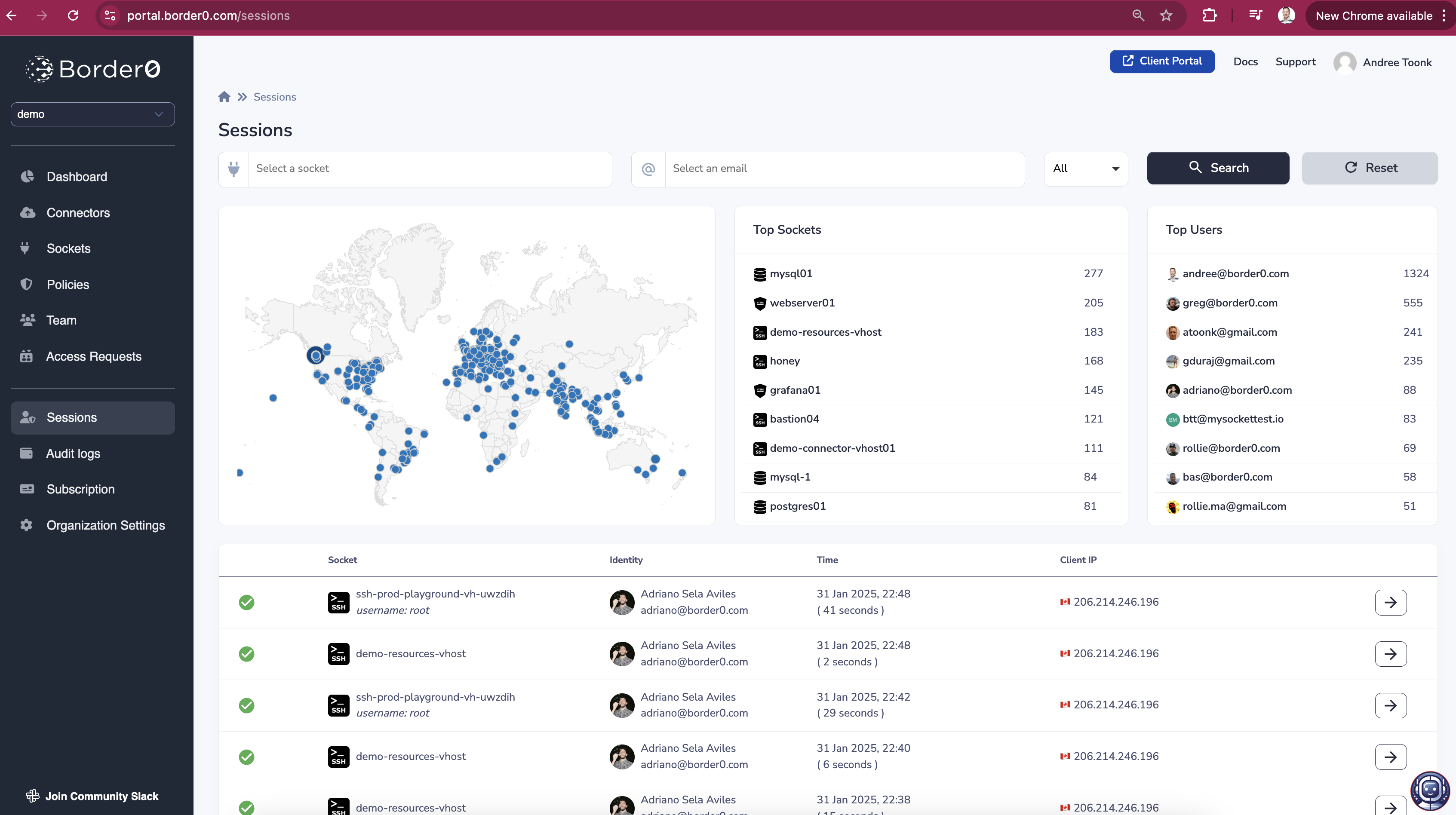
Session overview
🔍 What Information Does a Session Contain?
Each session contains rich contextual data, answering key security and audit questions:
- Who? → The single sign-on identity of the user or service account.
- What? → The resource (Socket) that was accessed.
- Where? → The geographic location (City, Country) and originating IP of the user.
- When? → The date and time of the session.
- What Happened? → A session recording, capturing everything from SSH commands to database queries, to HTTP session replays and even Kubernetes API requests.
This provides administrators with deep visibility into every connection, not just IP addresses and ports—but the full context behind who did what and when.
Advanced Flow logsIf you're familiar with VPC Flow Logs or NetFlow, think of Border0 Sessions as flow logs on steroids—with identity-aware data, resource context, and session recordings.
Listing sessions
As an administrator, you can request all sessions from the portal using the "Session Logs" link in the left-hand menu or using this URL: https://portal.border0.com/sessions
From there, you will find a list of all Sessions; these are network connections going to your various Sockets.
This overview gives you a quick overview of who accessed what resources when. By clicking on a session you'll be able to see more details as well as a recording of a session allowing you to see all the commands executed.
Advanced Firewall logsThink of this view of a modern Firewall log. Instead of just seeing IP addresses and Port numbers, administrators have access to far more context. Including the actual identity of the user, the resources that was accessed and the ability to watch back a video replay of the session.
Session Details
By clicking on a session you'll be able to see all the details for this session, including the ability to replay the recording for a session (assuming recording is enabled for the Socket).
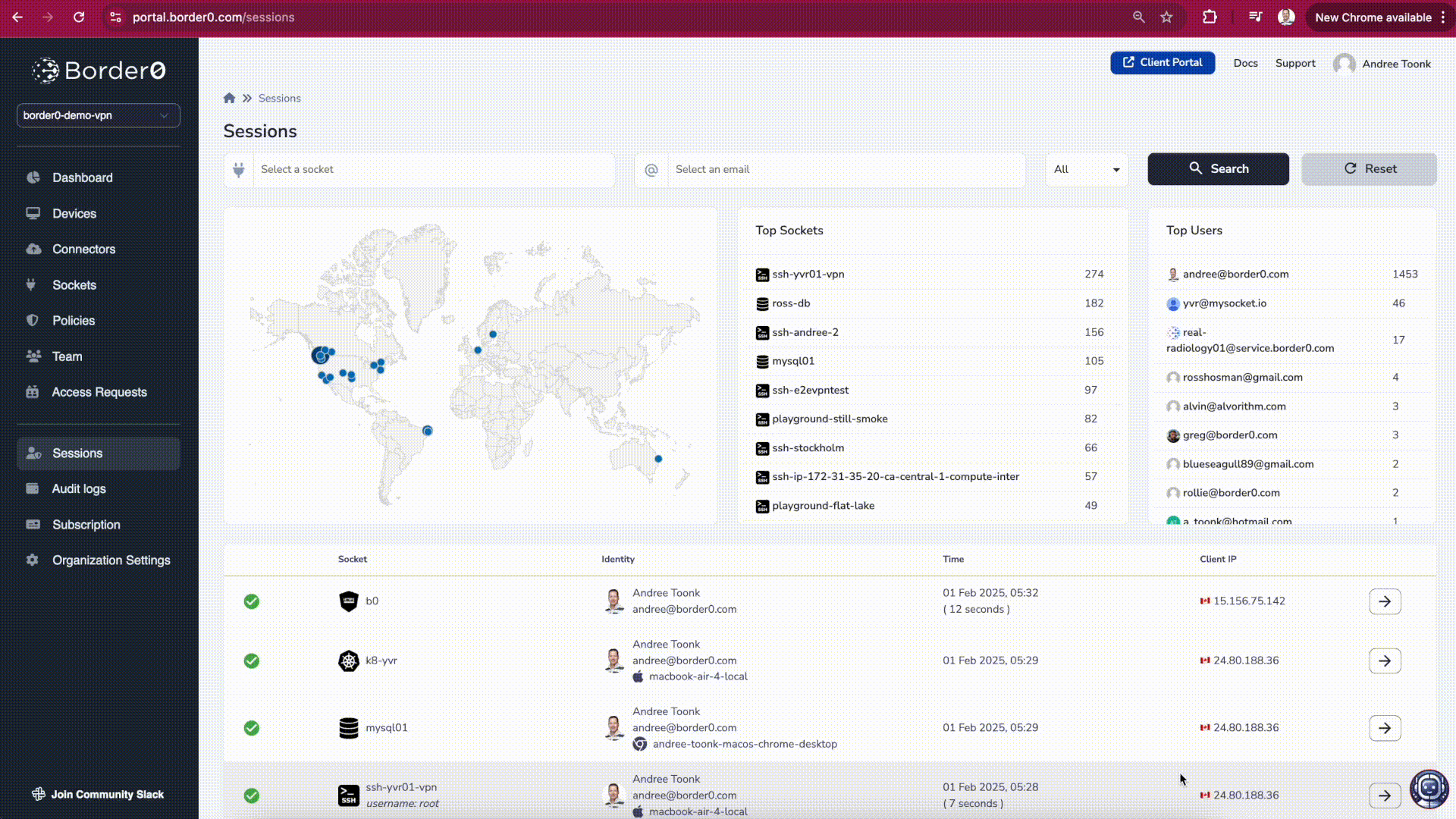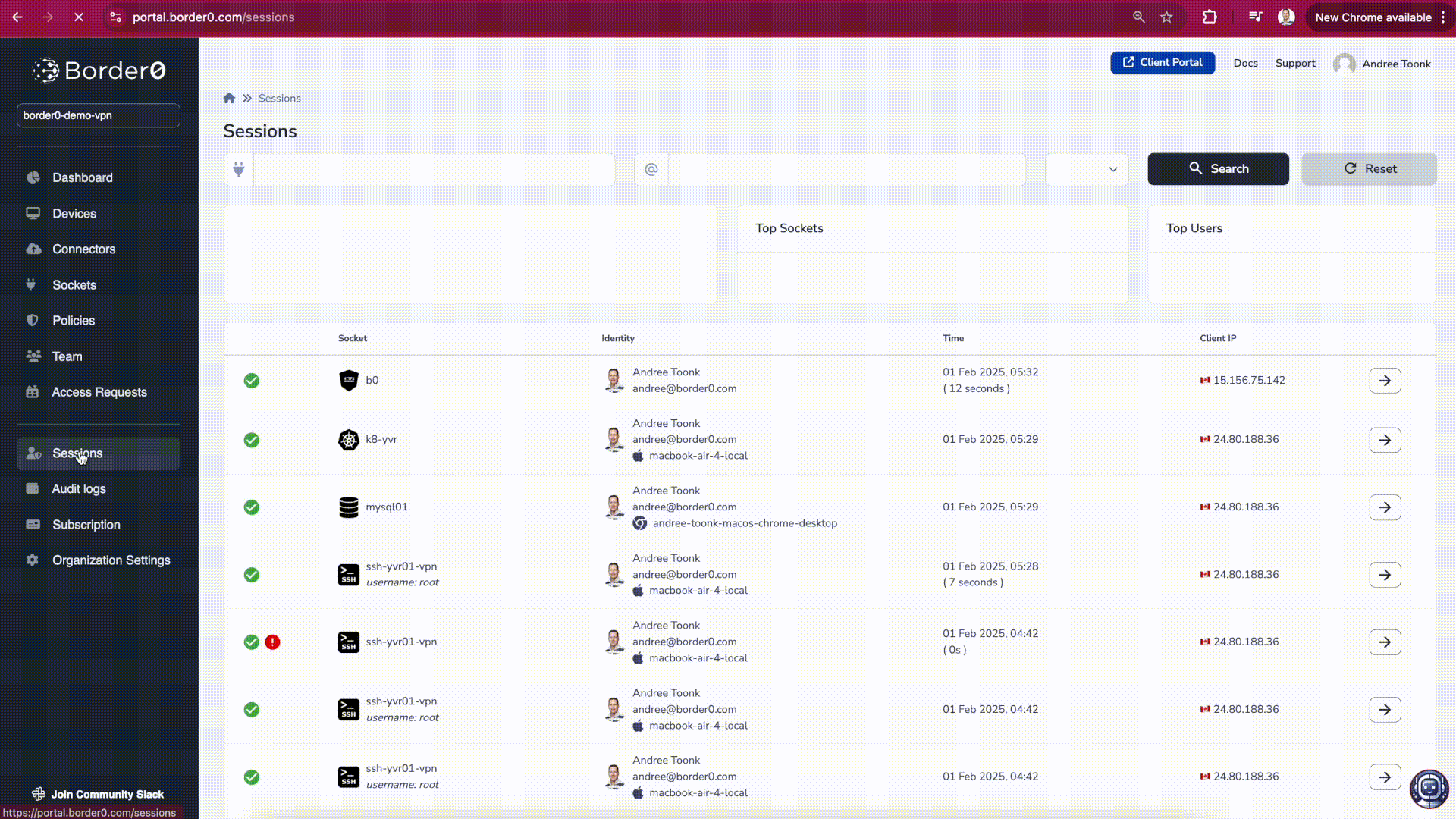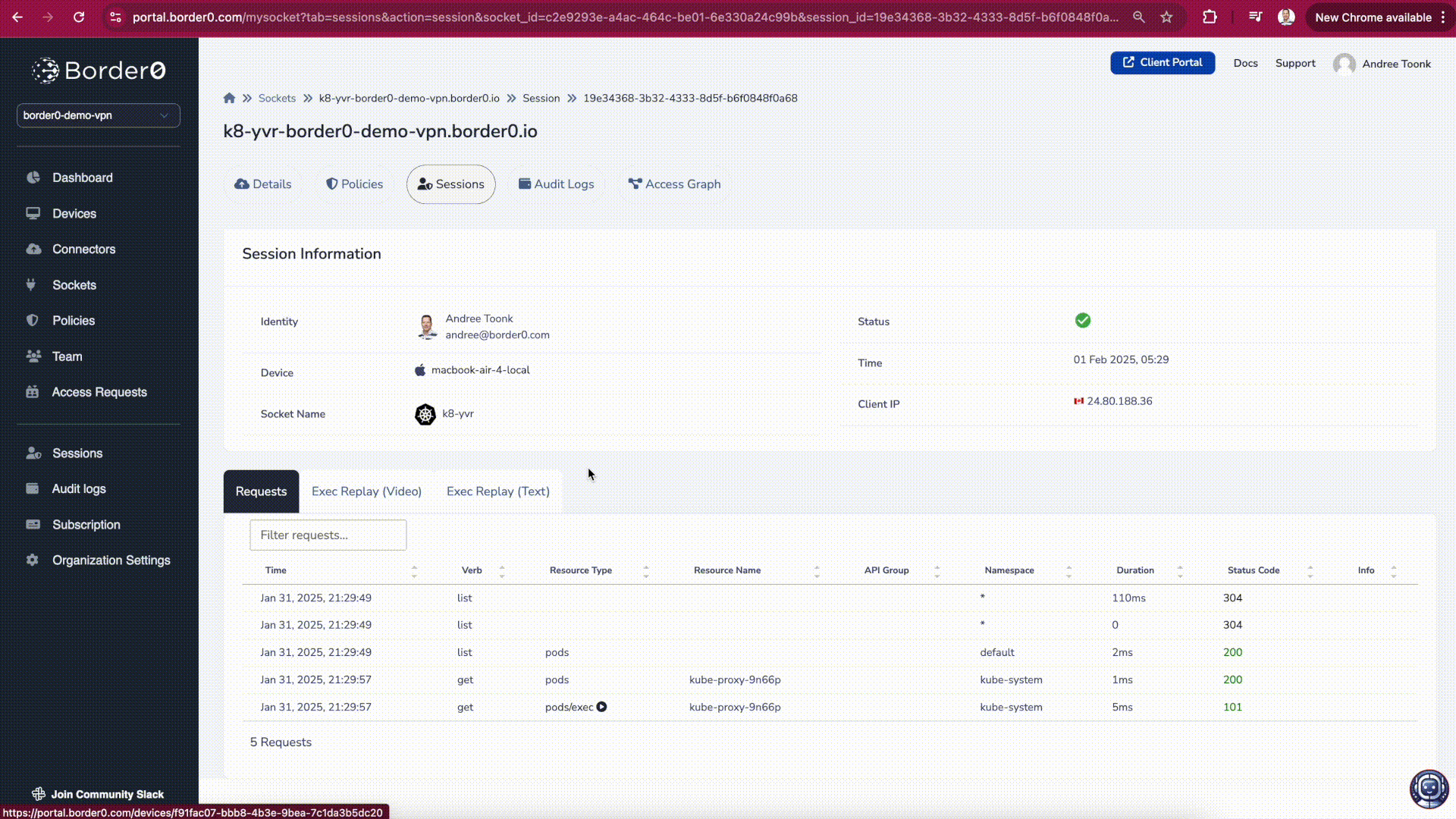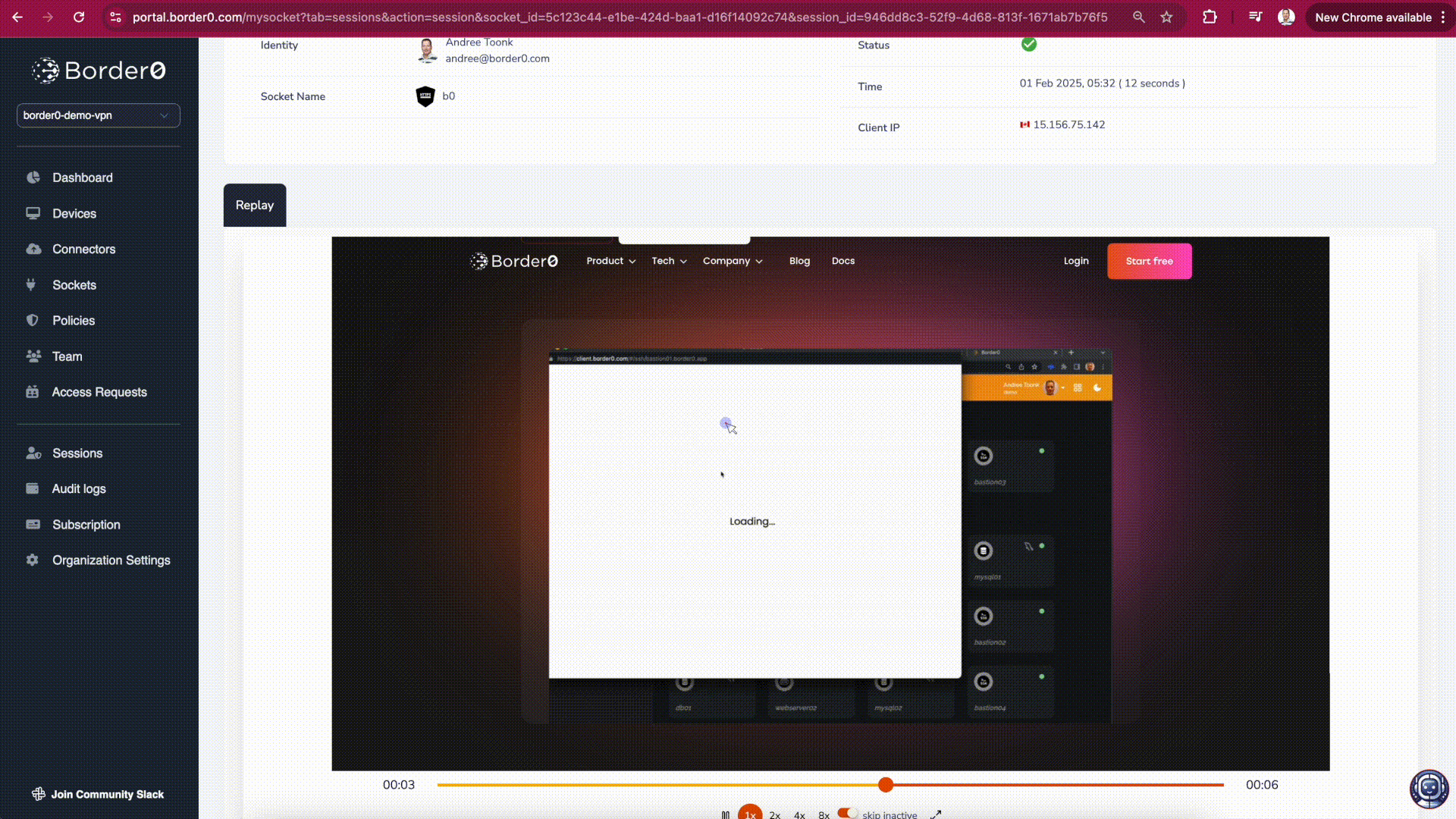
Session details and recording
Depending on the recording type, multiple tabs may be available:
- Video Tab → Displays a movie-like replay of the session, capturing all user actions.
- Text Tab → Provides a text dump of the session, ideal for uploading to a SIEM or conducting log analysis.
- Events Tab → Contains additional session metadata, including denied access attempts and details on the client software used during the session.
Session recording is currently supported for the following resource types:
- SSH (SSH, Docker, SSM, EC2, ECS)
- Kubernetes
- Databases
- HTTP
These tabs offer multiple perspectives on session activity, ensuring you have the information needed for auditing, compliance, and security investigations.
Interacting with Session using the API
We can use our API to ingest session logs by 3rd party systems such as a SIEM.
API Admin TokenNote: to use the API. You need an admin token. To retrieve an admin token execute
border0 login; this will write the token to~/.border0/token.
Below is a simple example. This will request the 100 most recent session logs
curl -X "GET" \
"https://api.border0.com/api/v1/sessions?page=1&page_size=100" \
-H "x-access-token: $(cat ~/.border0/token)" Session Details using the API
Use the example below to request the details of an individual session using the API.
$ curl -s -X "GET" \
"https://api.border0.com/api/v1/sessions?page=1&page_size=1" \
-H "x-access-token: $(cat ~/.border0/token)"
{
"pagination": {
"current_page": 1,
"next_page": 2,
"total_records": 1509,
"total_pages": 1509
},
"session_logs": [
{
"session_id": "93227a7e-8724-4be5-a5c5-2729f615ac50",
"socket_id": "432b9498-7762-45b9-8bb7-92f16158ff4a",
"start_time": "2022-10-10T04:46:50Z",
"last_seen": "2022-10-10T04:46:51Z",
"user_email": "[email protected]",
"server_name": "my-http-service3-acme.border0.io",
"server_port": "443",
"client_ip": "192.0.1.202",
"client_port": "62593",
"audit_log": false,
"name": "Andree Toonk",
"picture": "https://lh3.googleusercontent.com/a/ALm5wQSGWCa0NU3SKscuSvsYxhp-TmRR06_wrS=s96-c",
"sub": "xyx-bcb6-4997-89d3-xxxx",
"nickname": "",
"killed": false,
"session_type": "http",
"sshuser": null
}
]
}
PaginationNote how we requested the first page and only one item per page. We also get back some additional information for pagination, such as how many other items are available.
This API endpoint can feed data into your log system or SIEM.
Similarly, you may request the session replay like this:
curl -X "GET" \
"https://api.border0.com/api/v1/session/<socket_id>/<session_id>/session_log" \
-H "x-access-token: $(cat ~/.border0/token)" To kill a session using the API use:
curl -X PUT \
"https://api.border0.com/api/v1/session/<socket_id>/<session_id>" \
-H "accept: application/json" \
-H "x-access-token: $(cat~/.border0/token)" \
-H "Content-Type: application/json" \
-d '{
"killed": true
}'
Updated 10 months ago
