Architecture and Key Concepts
Border0 platform
Border0 is a globally distributed service designed for high availability and low latency. Leveraging proxy, tunnel, and API servers across the world, it operates through an anycast network with 102 Points of Presence across 86 cities in 48 countries. This ensures that you get fast, secure access to your resources, wherever you are, without the need for additional management effort.
Sockets (aka Services)
At the core of Border0 are Sockets, which represent the services you make available to users. These can be any service that you need to securely expose, such as:
- Web services (HTTP(s))
- SSH services
- Database services (MySQL, PostgreSQL, MSSQL, elastic search, MongoDB, snowflake)
- VNC
- RDP
- Generic TCP services
- Subnet routes (ipv4 and ipv6 networks)
- exit nodes, ie Internet gateways (0.0.0.0/0 or ::/0)
The term "Socket" is borrowed from network programming, where a socket is an endpoint for communication between systems. Border0 treats these as the application-aware proxies that handle connections securely.
Policies
Policies are key to managing access to your services. By default, no one has access to your sockets unless you explicitly grant it. Think of Border0 policies as enhanced firewall rules. Unlike traditional firewalls, which restrict access based on IP and port, Border0 allows you to control access with more granular conditions such as:
- Who (the identity of the user)
- What (the specific resources/sockets)
- When (the time of day or date)
- Where (IP addresses or countries)
There are two types of policies:
Organization-wide policies: These apply automatically to all sockets in your organization.
Socket-specific policies: These can be manually linked to individual sockets.
This fine-grained control ensures that only authorized users can access your services under specific conditions.
Sessions
A Session represents the connection between a user and a service. allowing you to track who accessed what resource, when, and from where. Each session log include details such as:
- User Single sign-on identity
- IP address
- Geo Location
- Device information
- Connection time and duration
Additionally, Border0 allows for session recording, which means you can replay sessions for services like SSH, Database, and HTTP to review exactly what happened during a session. This is particularly useful for security audits or troubleshooting.
Tunnels
Tunnels are secure, encrypted connections between the Border0 Connector and the user's device, enabling seamless access to private resources.
How Tunnels Work
- Encryption: Tunnels use WireGuard, a modern, high-performance VPN protocol, to ensure end-to-end encryption.
- Automated Management: The Border0 platform automatically manages tunnel creation and orchestration, requiring no manual setup from the user.
- Seamless Connectivity: Whether connecting to SSH, databases, Kubernetes, or internal web applications, tunnels ensure secure, low-latency access without exposing services to the internet.
Connector
The Border0 Connector acts as a bridge between your infrastructure and the Border0 platform, serving as an identity-aware application proxy. It’s the workhorse of the system, handling critical functions like:
- Session termination – It securely terminates all client sessions.
- Policy enforcement – Evaluates policies in real-time to control access.
- Session recording – Captures session data for auditing and replay (SSH, Database, HTTP).
- Service discovery – Automatically detects available resources.
- Secrets injection – Seamlessly injects credentials and authentication tokens.
The Connector is deployed inside your infrastructure, ensuring that sensitive traffic remains private. Connections between clients and the connector are fully encrypted, meaning Border0 never sees your traffic, giving you full control over your security while benefiting from the platform’s ease of use.
Account & Organization Structure
Account
Think of the account as the root account for your Border0 subscription. Your Border0 account includes one or more organizations. Each account is tied to a unique set of Border0 resources and permissions.
Organization
An organization is a logical grouping of your Border0 resources, including sockets, policies, and users. Each organization is assigned a unique name that identifies it within Border0 and needed to log in.
Administrators
Administrators are users who have the ability to manage Border0 accounts and resources. An administrator can be assigned to multiple organizations, and their permissions can be customized based on their responsibilities within each organization. This allows for fine-grained control over who can manage which resources.
Border0 CLI tool
The border0 CLI tool is a rich CLI tool that allows administrators and end-users to interact easily with the Border0 API and Platform. Administrators can use it to manage resources such as sockets, policies, and start tunnels.
End users (clients) can use the Border0 CLI tool to connect to resources made available by administrators through the Border0 Platform. For example, an SSH resource would be accessed like this: border0 client ssh[email protected]
The Border0 CLI is packaged with the desktop app and can be downloaded from our download page here: https://border0.com/download
Desktop App
The Border0 Desktop App offers a modern graphical user interface (GUI) for end users, streamlining the process of connecting to resources, selecting exit nodes, and discovering available services. With just a single click, users can securely access any resource they have permission for, including servers, databases, web applications, desktops, and Kubernetes clusters.
Client Portal: Secure, Clientless Access to Resources
The Border0 Client Portal is a WebAssembly (WASM)-based solution that allows users to securely access resources without installing any Border0 software on their desktop. This clientless approach makes accessing your services incredibly easy and seamless.
Key Benefits:
- No installation required – Access your resources directly from the browser.
- Easy resource discovery – A visual, intuitive interface helps users see what they have access to.
- Web-based access to critical services – Use SSH, databases (MySQL/Postgres), and even VNC directly in the browser.
- End-to-end encryption – With WASM-powered VPN technology, the Border0 client runs entirely in the browser, ensuring that connections remain fully encrypted and secure.
- Access Requests for Zero Standing Privileges (ZSP) – From the client portal users can request just-in-time access, enabling admins to grant time-limited permissions, reducing security risks.
This means users can connect to their infrastructure instantly, without any complex setup, making for a super smooth, almost magical end-user experience.
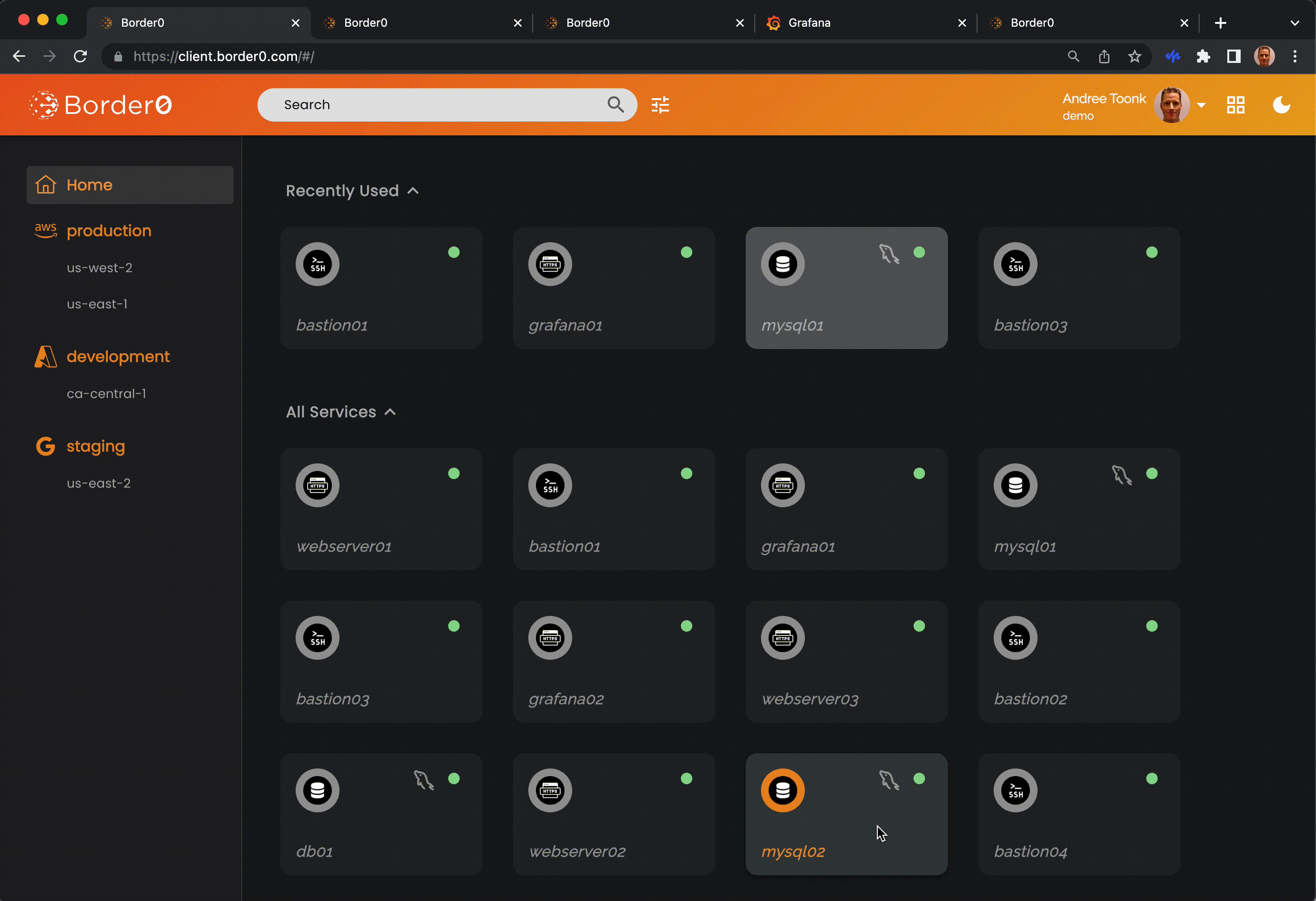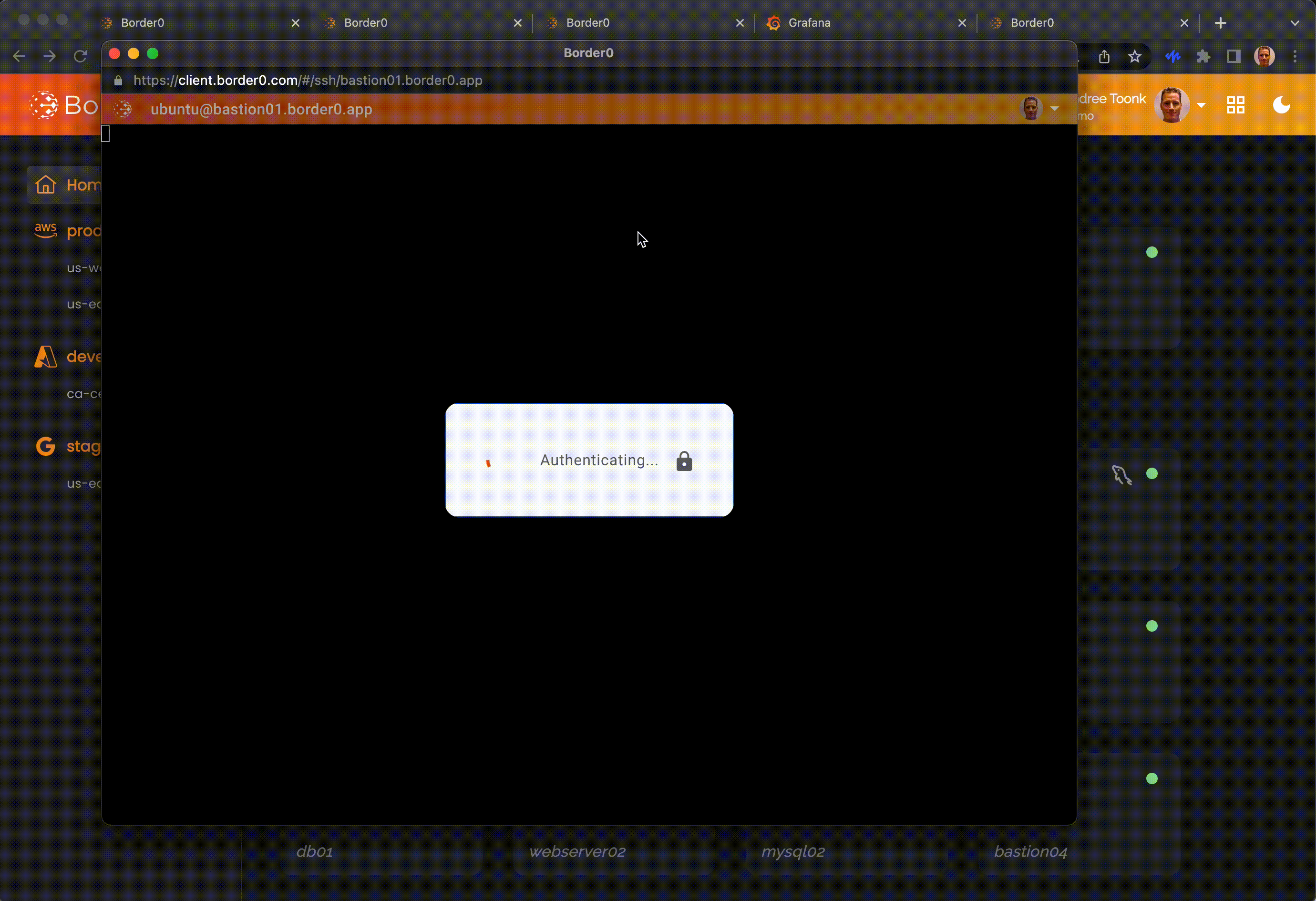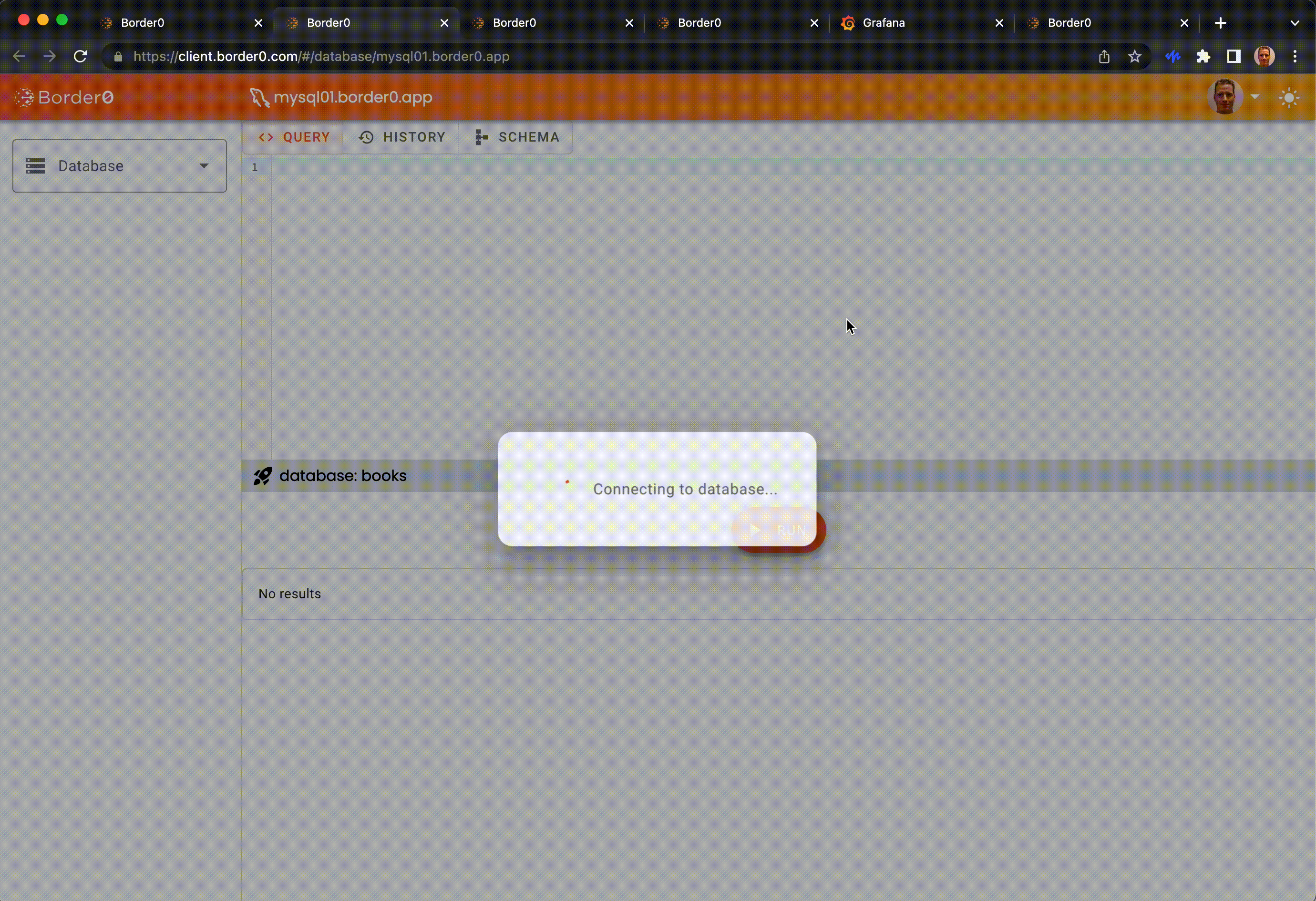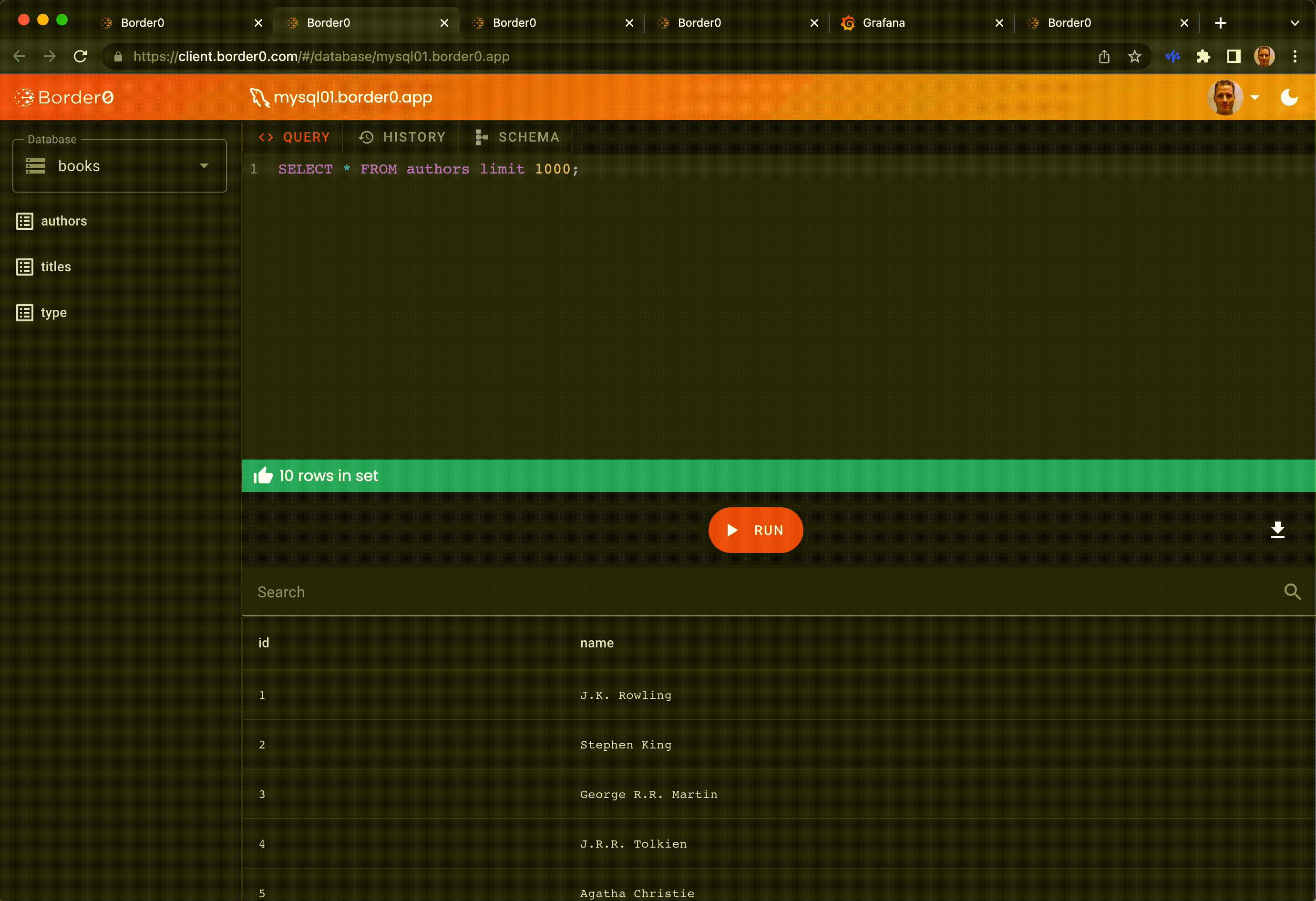
Border0 client portal
Updated 7 months ago
