Subnet Routing
Making Subnets available
Using border0, you can make internal subnet routes available to your clients. These can be routes to your private network, an AWS private VPC subnet (e.g., 10.10.0.0/16), or any other private subnet. Think of this as a split tunnel setup.
Creating a Subnet Router Socket
To make a subnet router socket available, follow these steps:
-
Create a New Socket: Click on "New Socket."
-
Select Subnet Router: Choose the "Subnet Router" socket type.
-
Configure the Subnet Router: A subnet router allows you to define a list of IP networks or prefixes that will be pushed to VPN clients, provided the policy matches (see below). These routes are always pushed (unlike exit nodes) and function as a typical split tunnel setup.
-
Provide Socket Details:
- Name: Give your subnet router a descriptive name (e.g., "aws-us-east2").
- Description (Optional): Add an optional description for clarity (e.g., "Access to the production 10.10.0.0/16 subnet").
- IPv4/IPv6 Prefixes: Specify one or more IPv4 or IPv6 prefixes that you want to route. For example:
10.10.0.0/16 192.168.1.0/24 2001:db8::/32 - Connector: Select the appropriate connector that has access to these subnets. This connector defines the egress point for traffic destined to these subnets. Note that the connector will NAT traffic to these subnets; this will ensure you don't have routing issues.
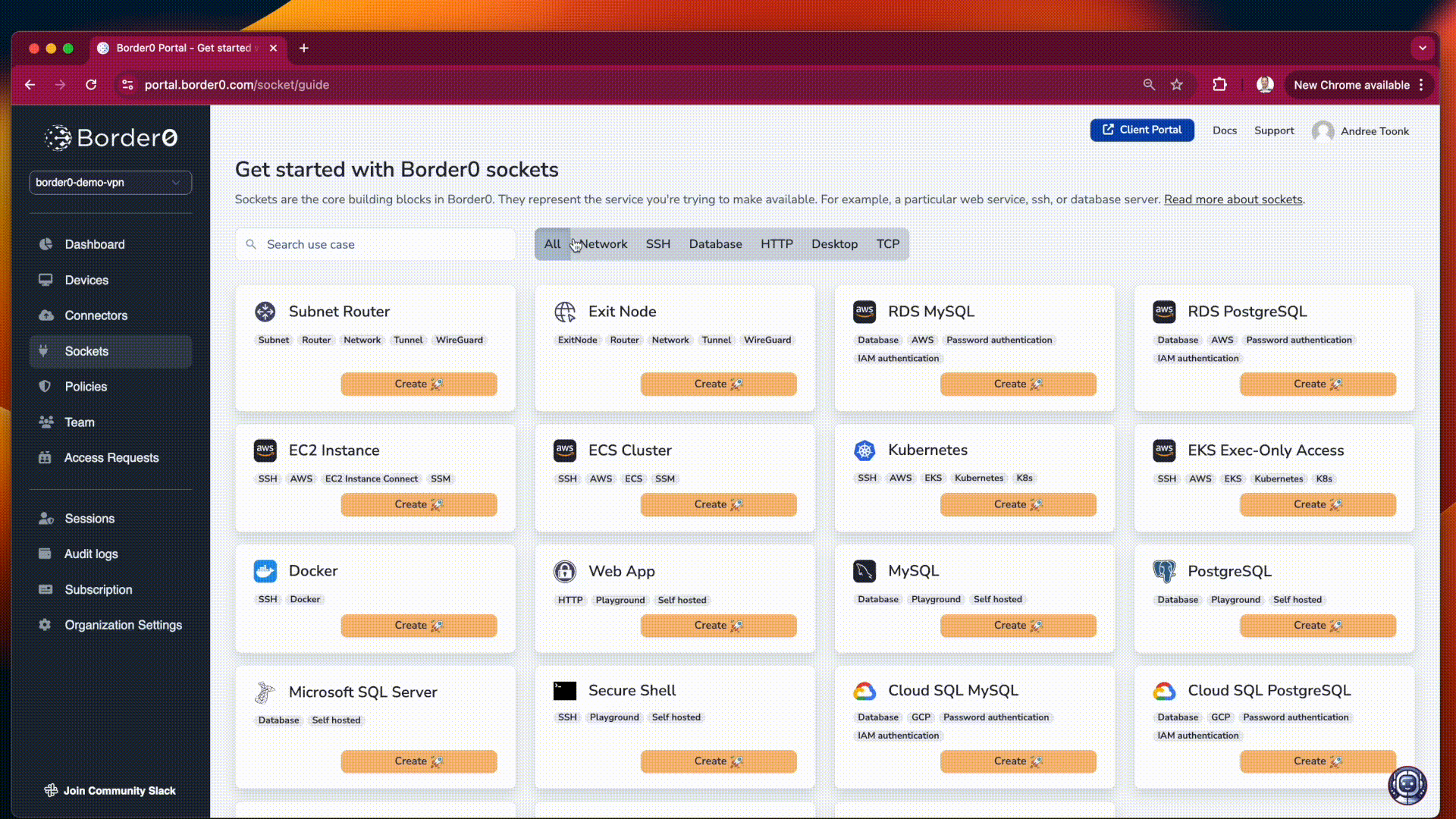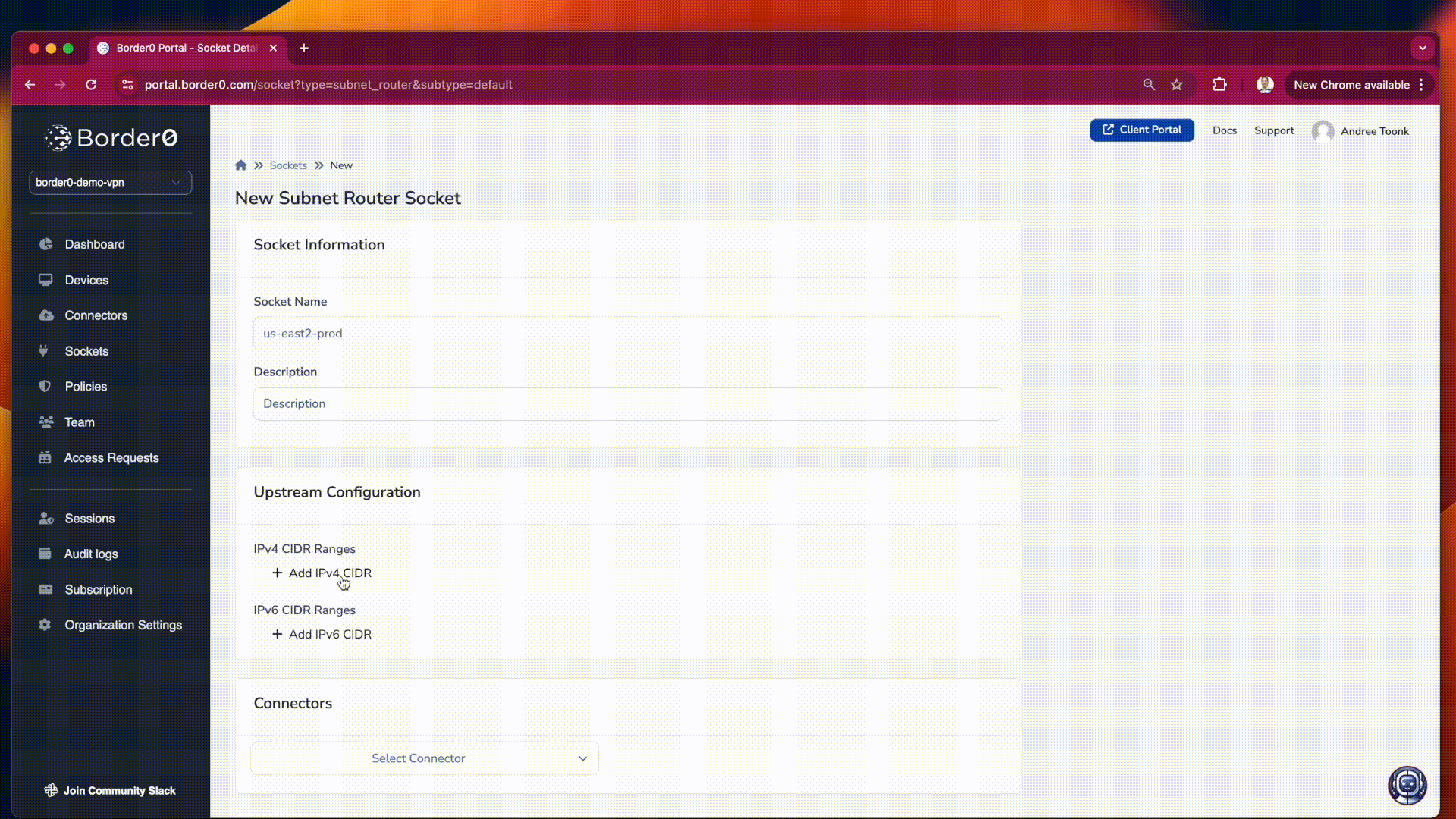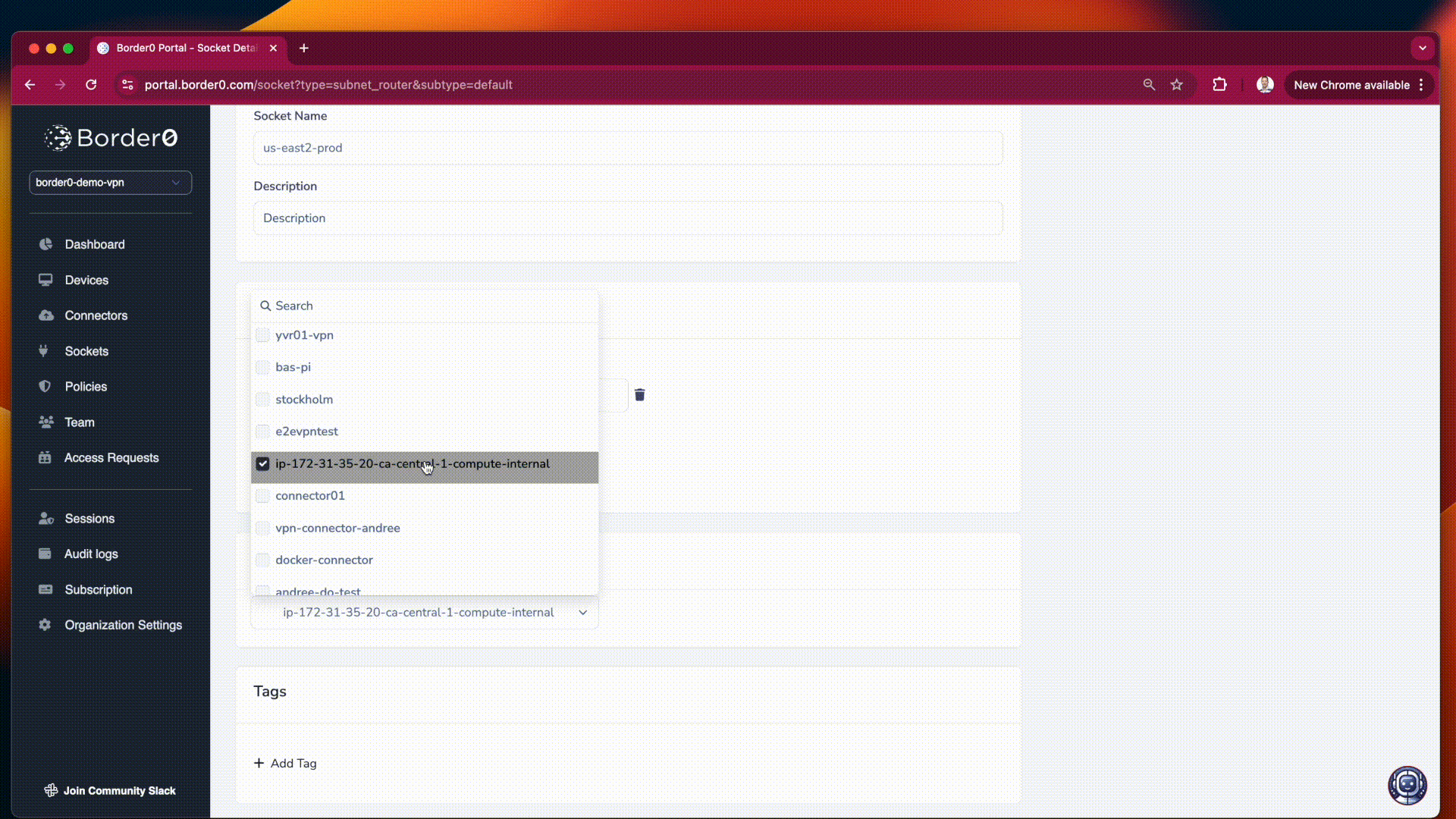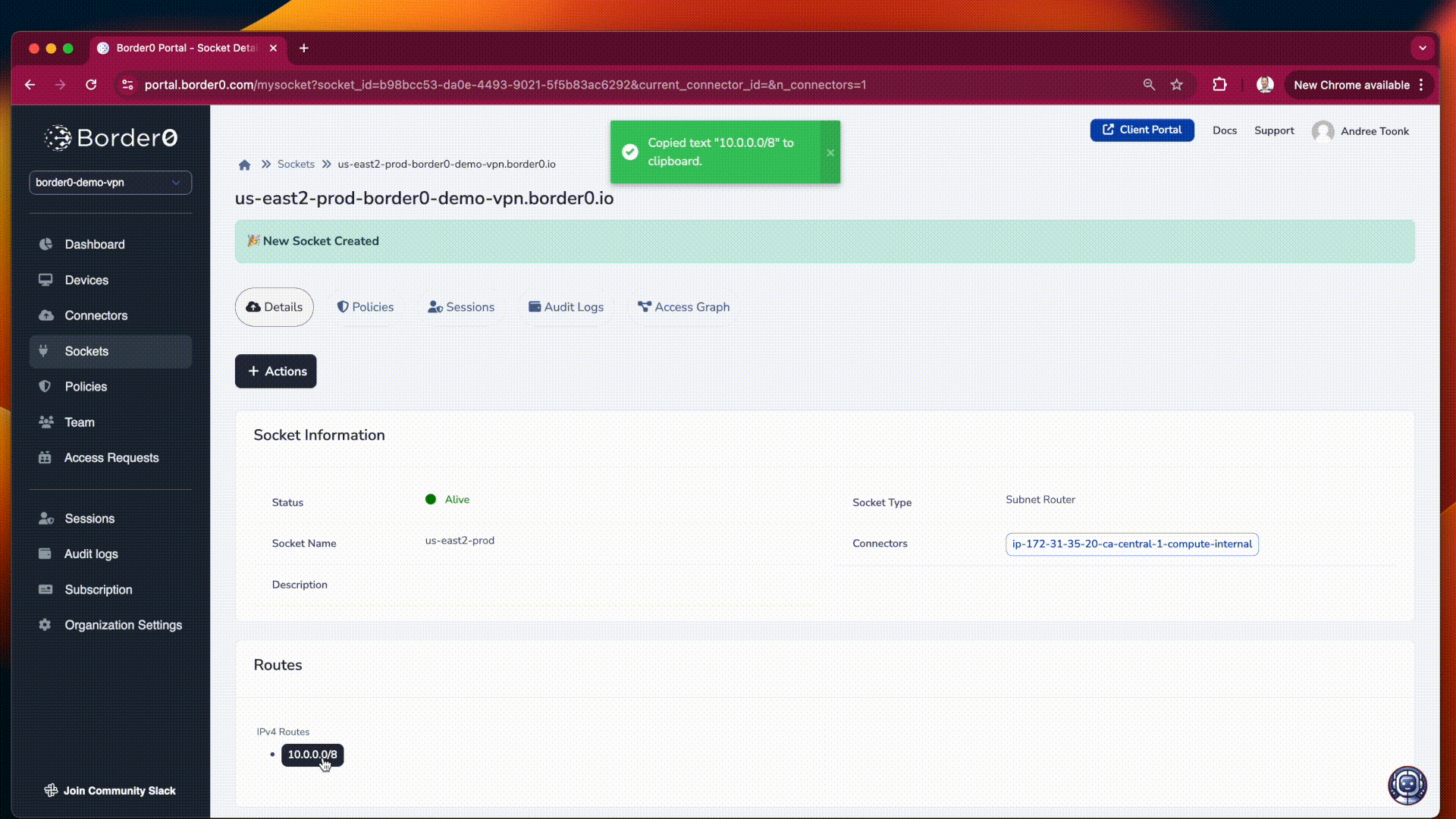
creating a subnet route resource
After creating the new socket, the defined routes will be automatically pushed to clients that are authorized to access this socket via policy. Clients with the appropriate policy will then be able to reach the specified subnets through the border0 connection.
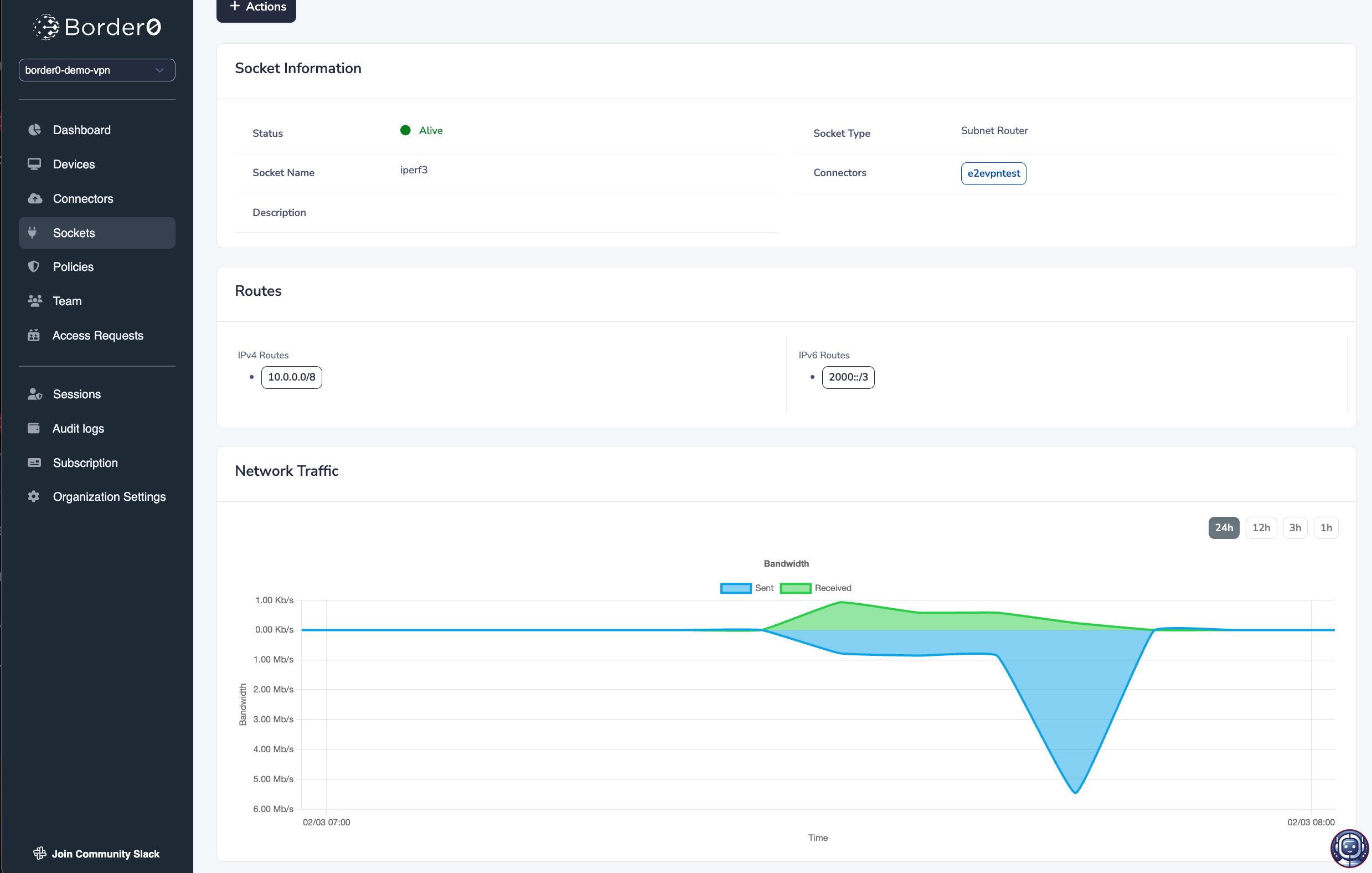
traffic statistics for your Subnet Router Socket
In the Border0 portal, you will find per Subnet Router Socket traffic statistics, allowing you to see how much traffic is being routed through your exit node socket.
Policies
To control which users have access to the subnet routes you've defined, you must configure the appropriate policies. Users who should have access to these subnets must have the network permission enabled in their policy.
This specific permission controls who receives VPN routing information, specifically for subnet routers and exit nodes. Without this permission, even if a user is connected to border0, they will not receive the routing information for the defined subnets, and therefore, will not be able to access them.
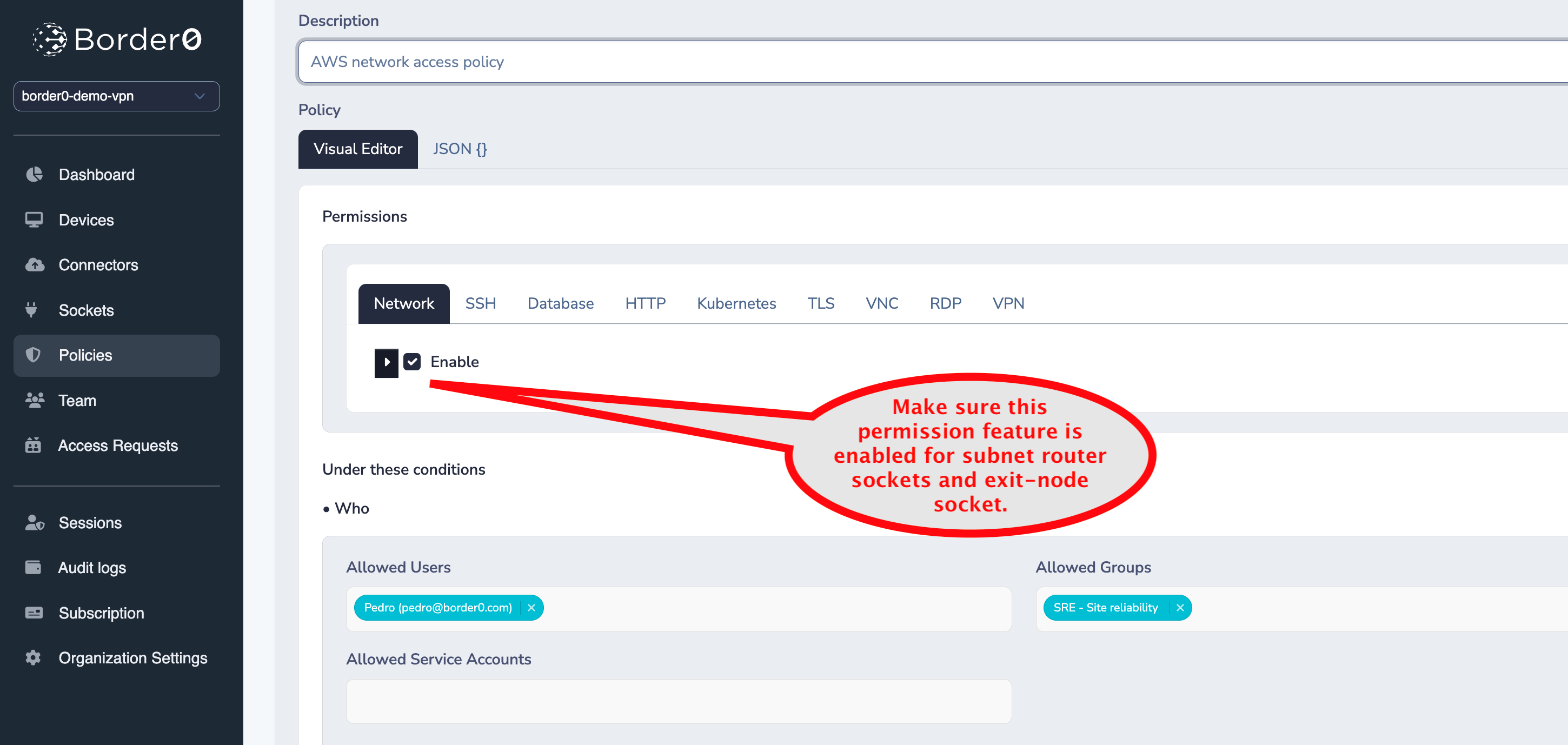
enabling network permissions in the Policy
By enabling this permission in the appropriate policy and assigning that policy to the correct users, you control who can utilize the subnet routes defined in your subnet router socket.
Troubleshooting and Validating
The easiest way to validate if a route is available on a client is by checking its routing table.
macOS:
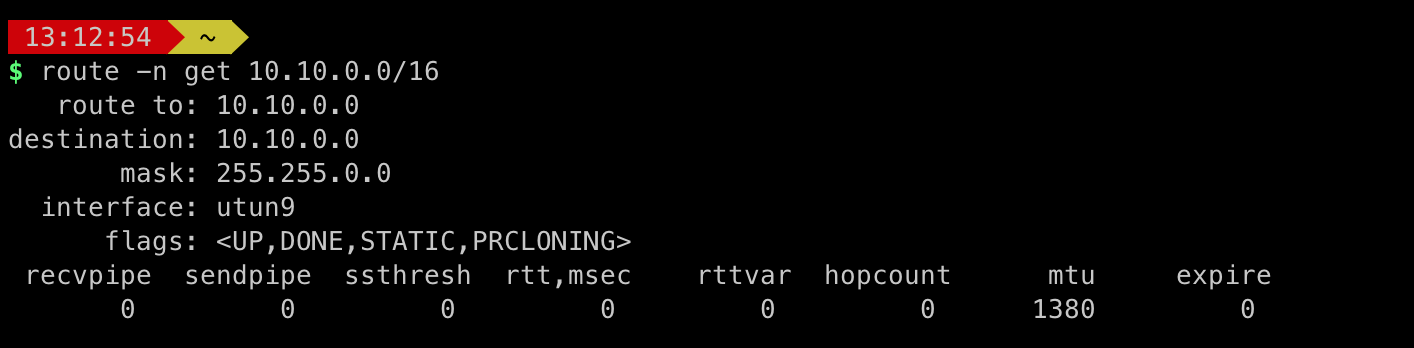
You can execute the following command to see the route to a given destination:
route -n get 10.10.0.0/16Validate that the route is present and points to the VPN tunnel interface, which typically starts with utun followed by a number (e.g., utun2).
Windows:
route print 10.10.0.0Linux:
ip route get 10.10.0.0/16If the routes are not present, make sure to:
- Verify Permissions: Validate that the client has been granted the network permission.
- Check Policy Linking: Ensure that the policy containing the network permission is linked to the subnet router socket. For example by checking the access graph.
- Client Connection: Confirm the client is actively connected to the border0 network.
If the routes are present, but connectivity is broken, consider these additional troubleshooting steps:
- Firewall Rules: Check local firewall rules on the client machine or connector that might be blocking traffic to the target subnet.
- Validate with
tcpdumpthat the traffic arrives on the connector. - Connector Configuration: Double-check the configuration of your connector. Ensure that it has access to the target subnets and is functioning correctly and iptables is configured correctly.
- Contact Support: If you're still unable to resolve the issue, contact border0 support for assistance.
Updated 10 months ago
